2022DASCTF Apr X FATE 防疫挑战赛
Crackme
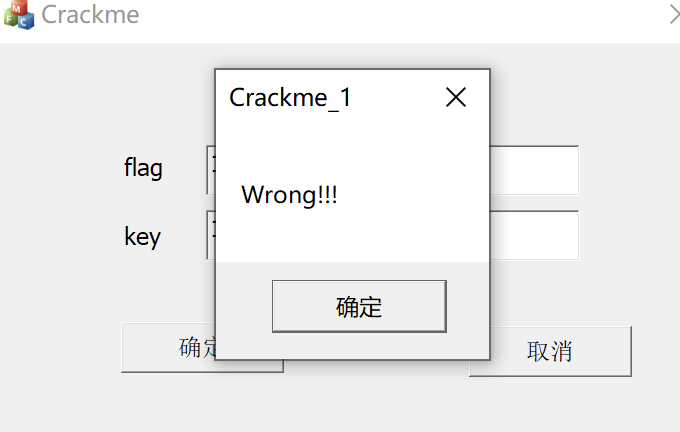
首先随便输入字符串,看看有什么反应,出现Wrong!!!的MessageBox,可以尝试去IDA搜索字符串,通过交叉引用找到逻辑函数,分析一下。
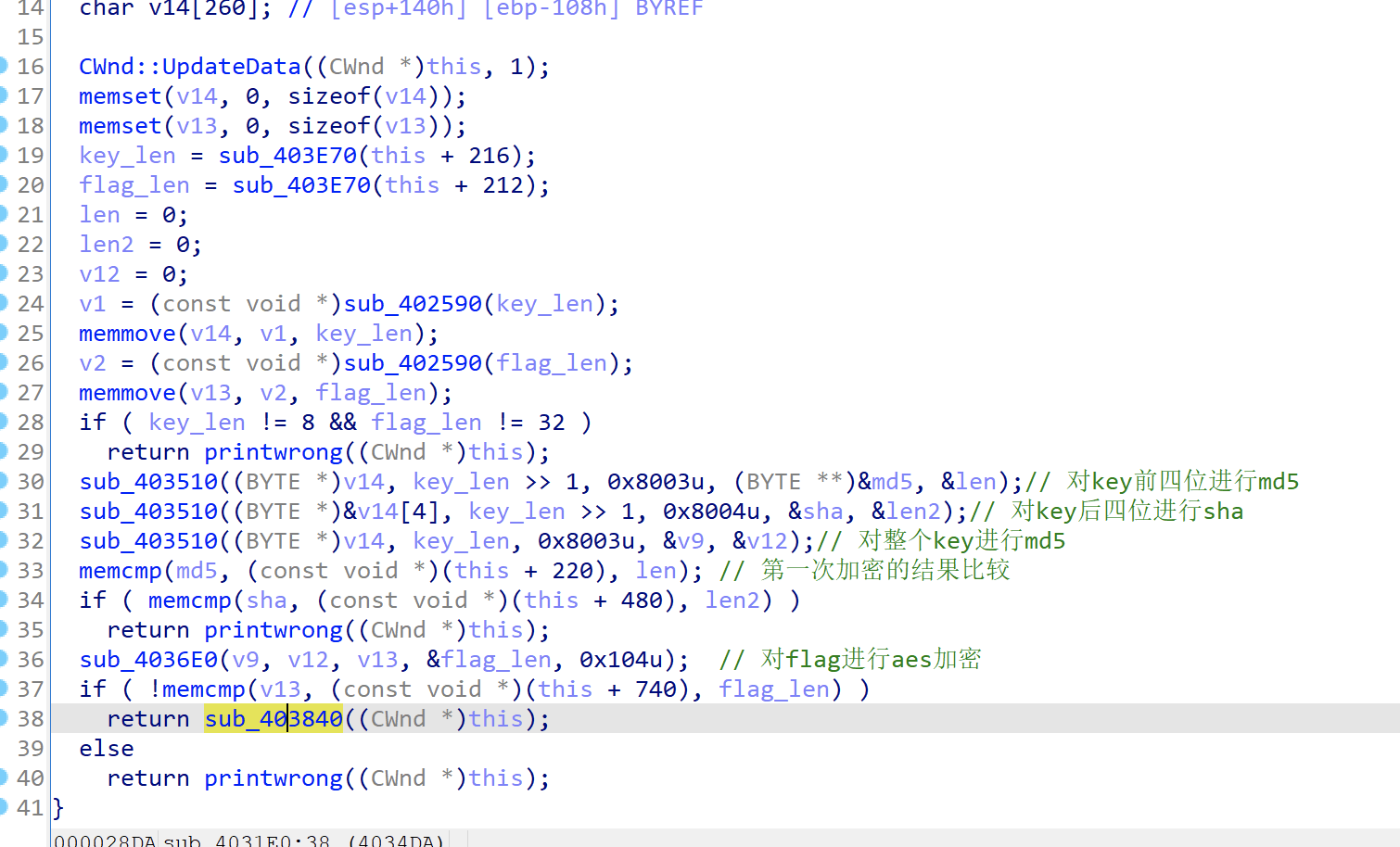
首先是key的长度是8位,flag的长度是32位,然后就是key的前四位进行某种操作sub_403510(后面会分析),然后同理对key的后四位进行同样的操作,最后是整个key,只不过三次的函数参数都不同,分析一下sub_403510函数
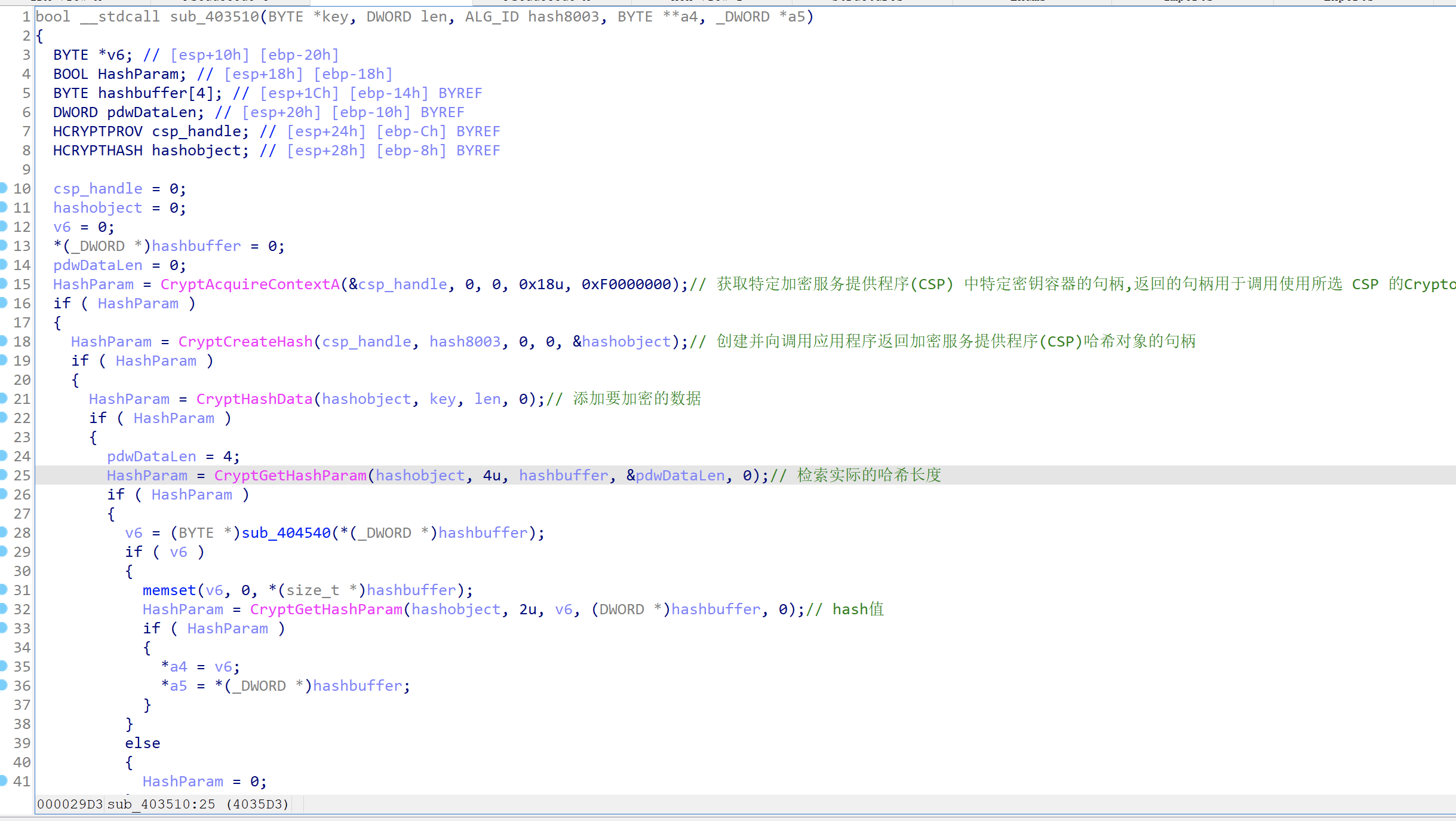
这里用到了windows的密码库,对应的API都可以在msdn上查到,主要注意CryptCreateHash的第二个参数,它决定了使用那种加密方式,查询网址
因此三次加密分别是md5、sha、md5,这些都是可以经过网站在线解密的,只不过需要动调获取密文。
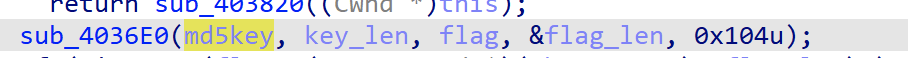
继续返回主函数分析,最后有个对flag的加密,然后就是加密后的flag与密文进行对比,我们分析一下sub_4036E0(),参数如下
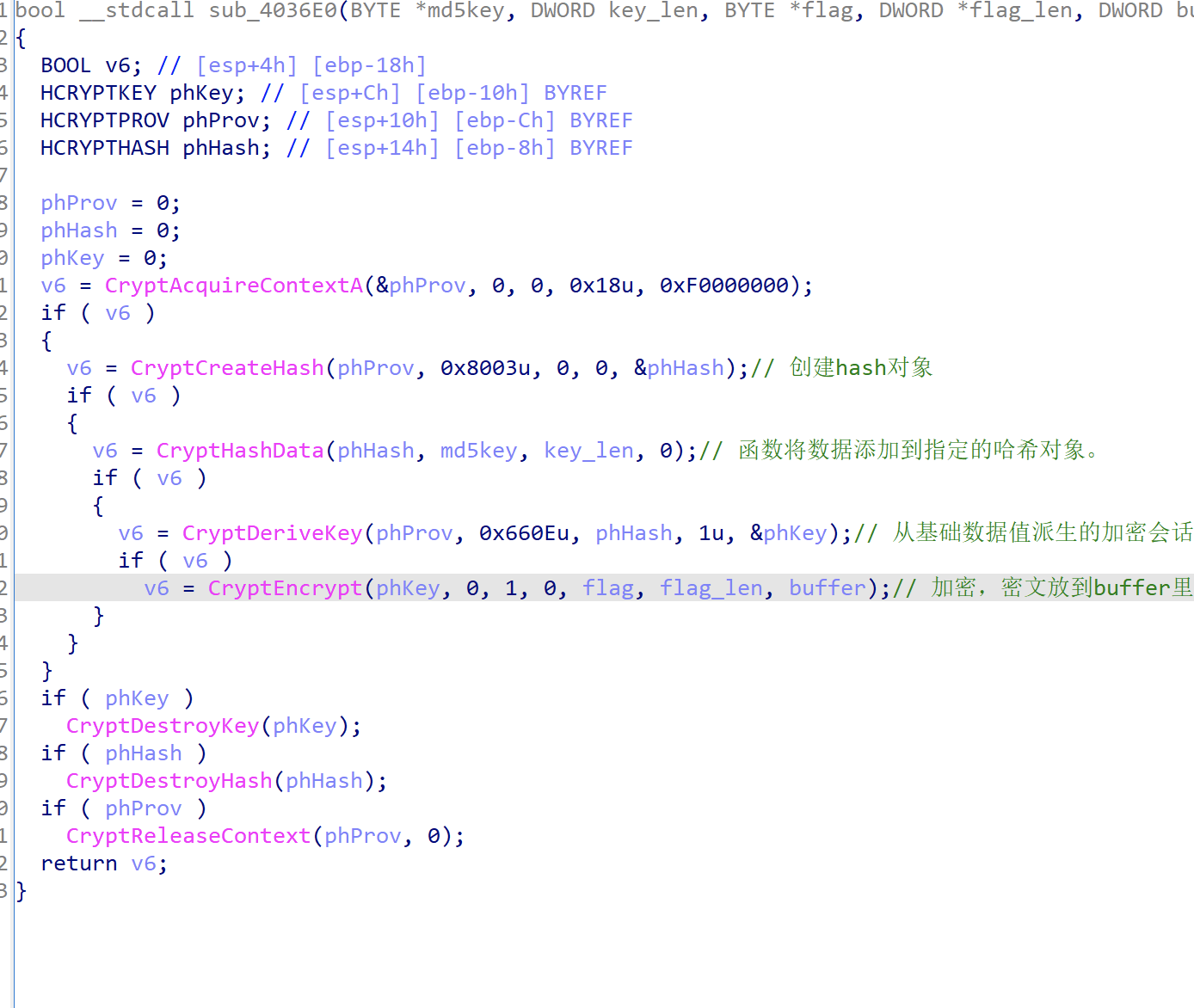
其中CryptDeriveKey第二个参数标识要为其生成密钥的对称加密算法的 ALG_ID结构,也就是对传入的flag进行加密,加密方式查询后为AES
然后我们就通过动调去拿数据,但是程序带有反调试,需要我们去进行反反调试,没有发现常见的反调试,在字符串中搜索Thread,发现ZwSetInformationThread,交叉引用过去
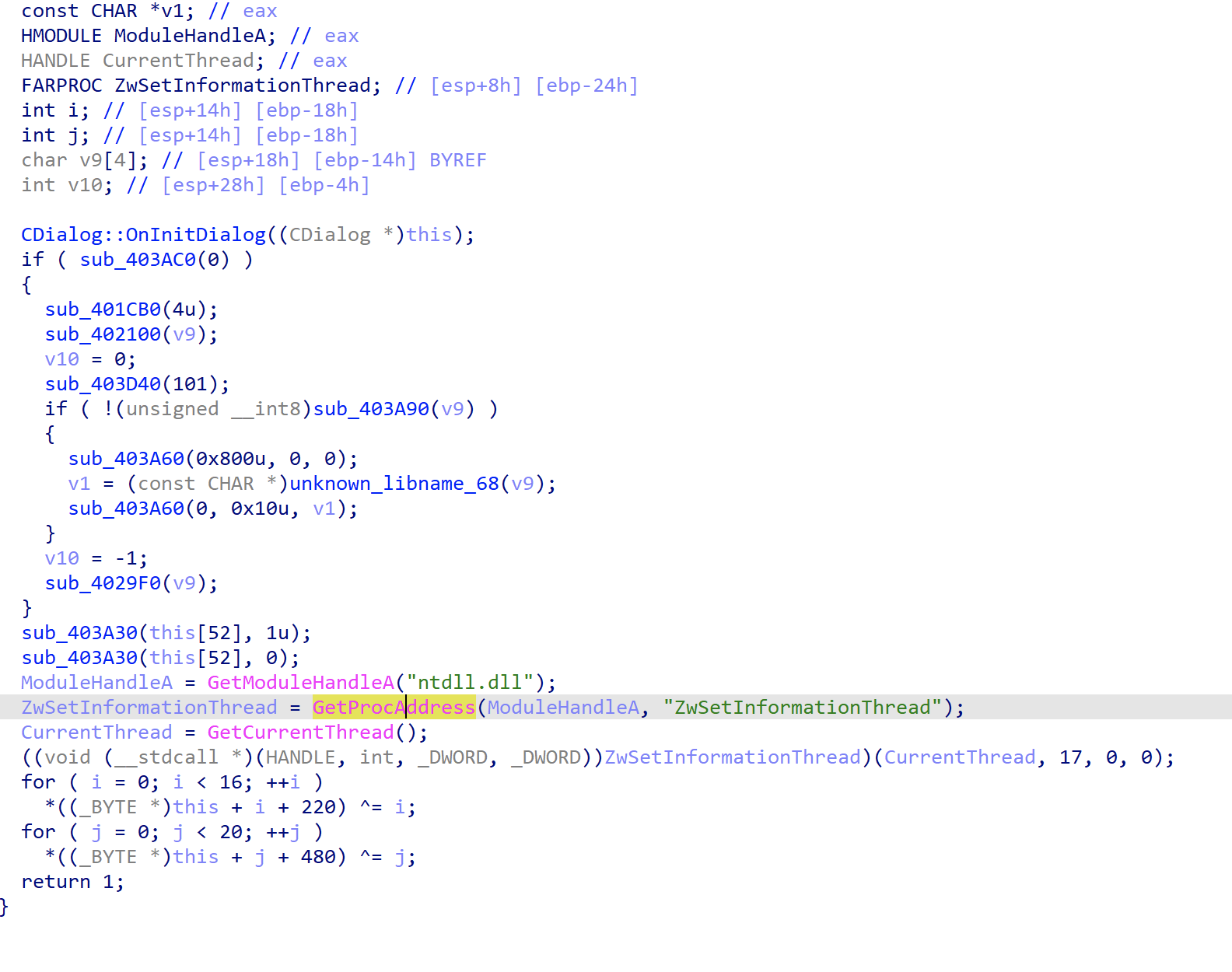
这里是自己实现的反调试,相关介绍
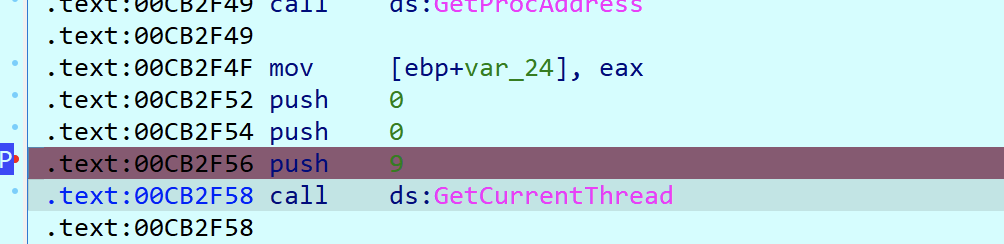
注意到该处 ZwSetInformationThread 函数的第 2 个参数为 ThreadHideFromDebugger,其值为 0x11。调试执行到该函数时,若发现第 2 个参数值为 0x11,跳过或者将 0x11 修改为其他值即可
我这里直接patch成0x9了
然后在第一次memcmp处下断点,获取key前四位md5后的值
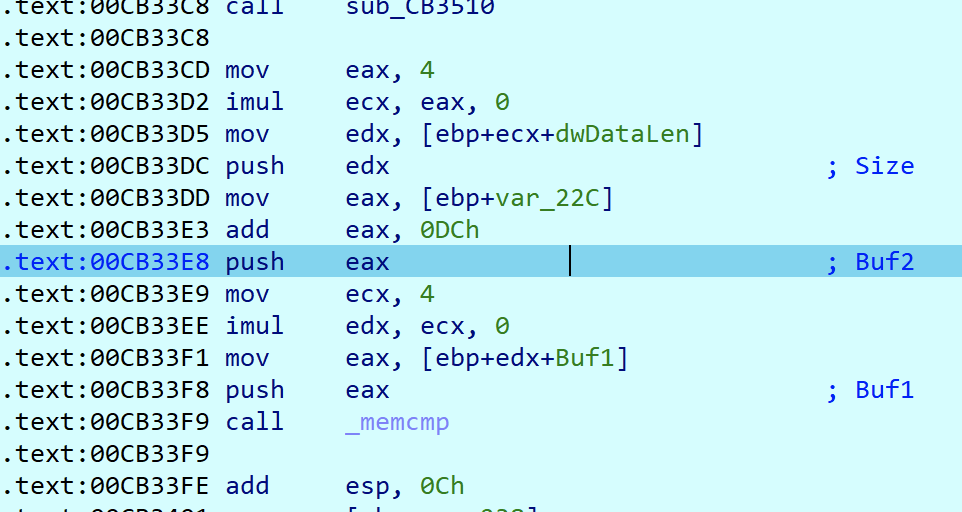
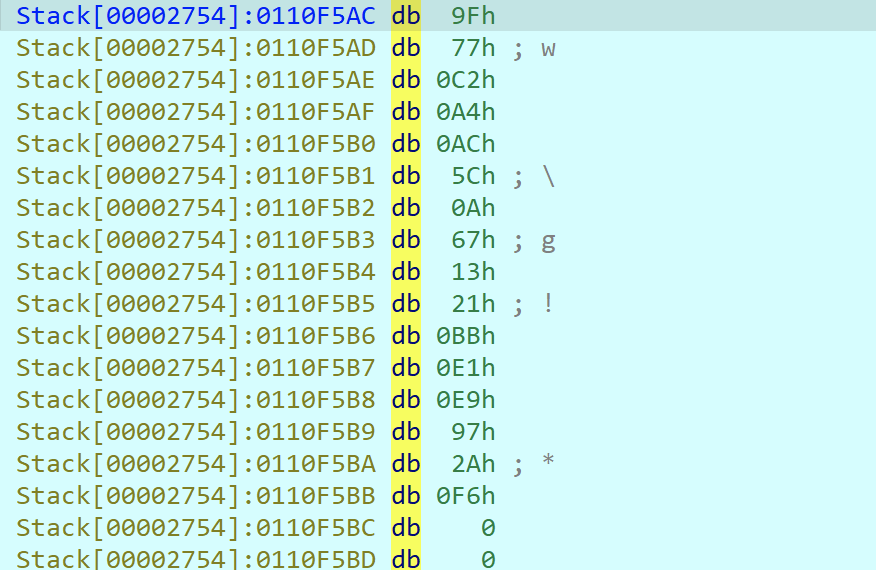
直接找个网站解一下试试
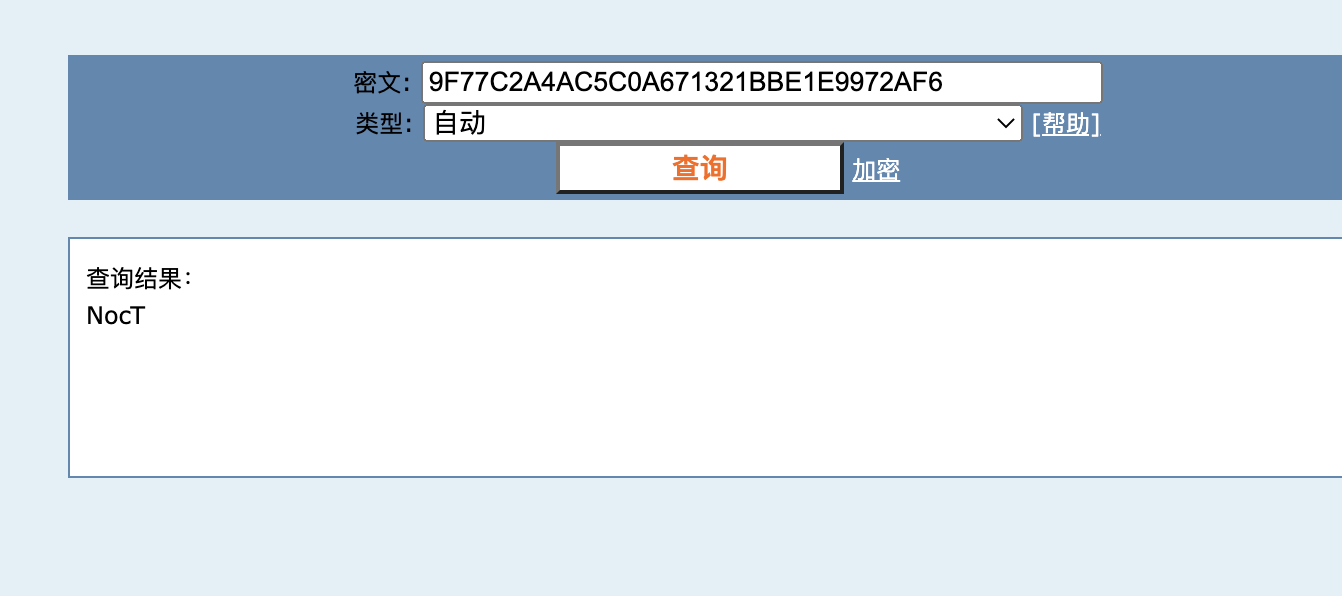
前四个字符为NocT,同理获取第二次sha加密的密文
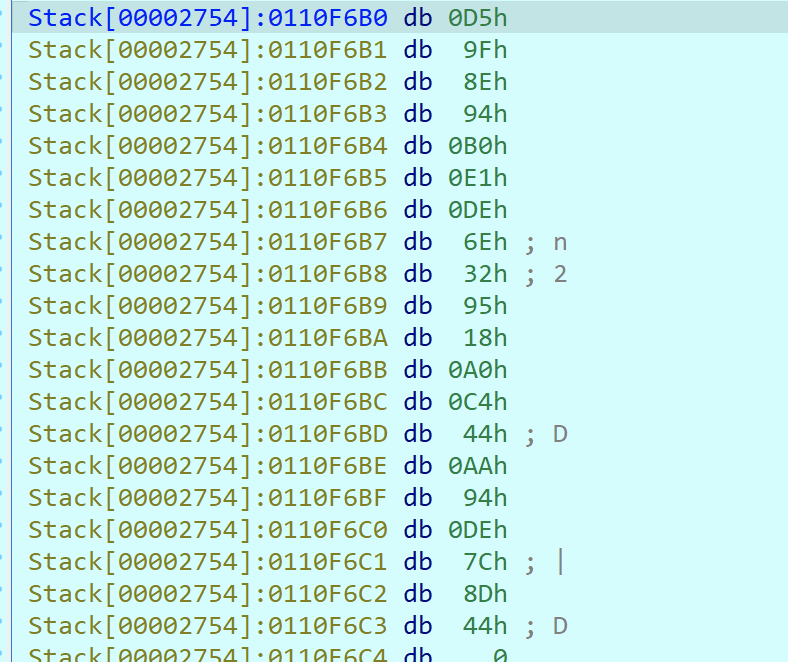
所以现在的key为NocTuRne,之后就是模拟调用win32 的aes解密api来解密的过程了,先调出密文
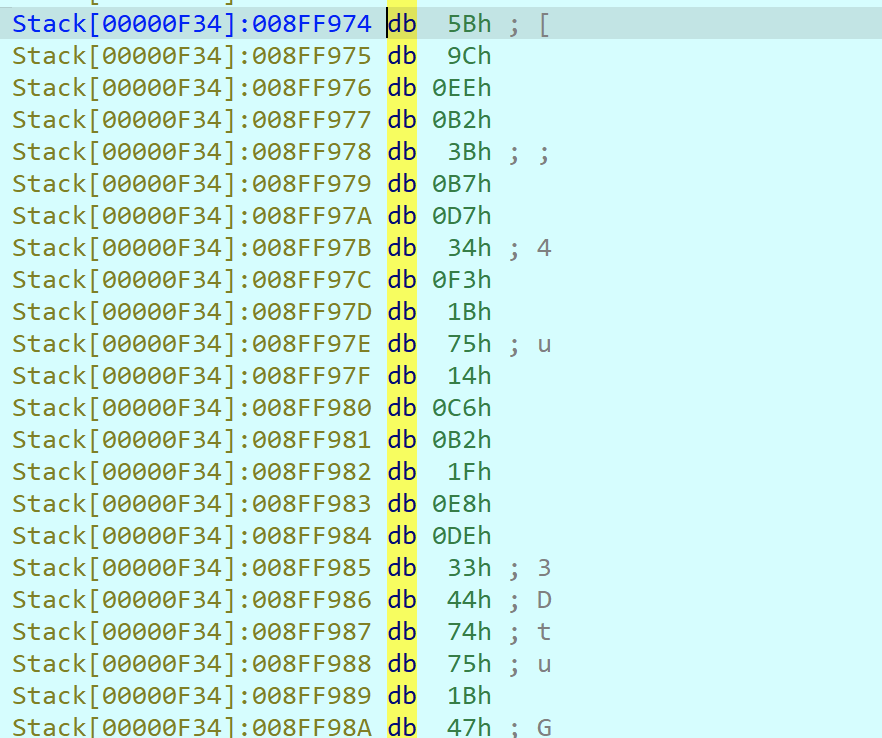
unsigned char ida_chars[] =
{
0x5B, 0x9C, 0xEE, 0xB2, 0x3B, 0xB7, 0xD7, 0x34, 0xF3, 0x1B,
0x75, 0x14, 0xC6, 0xB2, 0x1F, 0xE8, 0xDE, 0x33, 0x44, 0x74,
0x75, 0x1B, 0x47, 0x6A, 0xD4, 0x37, 0x51, 0x88, 0xFC, 0x67,
0xE6, 0x60, 0xDA, 0x0D, 0x58, 0x07, 0x81, 0x43, 0x53, 0xEA,
0x7B, 0x52, 0x85, 0x6C, 0x86, 0x65, 0xAF, 0xB4
};解密脚本
#include <Windows.h>
#include <stdio.h>
#include <wincrypt.h>
int main(){
BYTE pbData[] = {0x5c,0x53,0xa4,0xa4,0x1d,0x52,0x43,0x7a,0x9f,0xa1,0xe9,0xc2,0x6c,0xa5,0x90,0x90,0x0}; //key_buf,key被md5后
BYTE flag_encrypt[] = {0x5B, 0x9C, 0xEE, 0xB2, 0x3B, 0xB7, 0xD7, 0x34, 0xF3, 0x1B, 0x75, 0x14, 0xC6, 0xB2, 0x1F, 0xE8, 0xDE, 0x33, 0x44, 0x74, 0x75, 0x1B, 0x47, 0x6A, 0xD4, 0x37, 0x51, 0x88, 0xFC, 0x67, 0xE6, 0x60, 0xDA, 0x0D, 0x58, 0x07, 0x81, 0x43, 0x53, 0xEA, 0x7B, 0x52, 0x85, 0x6C, 0x86, 0x65, 0xAF, 0xB4,0x0};
DWORD dwDataLen = 0x10;
DWORD ddwDataLen;
DWORD* pdwDataLen = &ddwDataLen;
*pdwDataLen = 0x20;
BOOL v6; // [esp+4h] [ebp-18h]
HCRYPTKEY phKey; // [esp+Ch] [ebp-10h] BYREF
HCRYPTPROV phProv; // [esp+10h] [ebp-Ch] BYREF
HCRYPTHASH phHash; // [esp+14h] [ebp-8h] BYREF
phProv = 0;
phHash = 0;
phKey = 0;
v6 = CryptAcquireContextA(&phProv, 0, 0, 0x18u, 0xF0000000);
if (v6)
{
v6 = CryptCreateHash(phProv, 0x8003u, 0, 0, &phHash);
if (v6)
{
v6 = CryptHashData(phHash, pbData, dwDataLen, 0);
if (v6)
{
v6 = CryptDeriveKey(phProv, 0x660Eu, phHash, 1u, &phKey);// key的md5值再生成aes密钥
if (v6)
v6 = CryptDecrypt(phKey, 0, 1, 0, flag_encrypt, pdwDataLen);
printf("%s", flag_encrypt);
}
}
}
if (phKey)
CryptDestroyKey(phKey);
if (phHash)
CryptDestroyHash(phHash);
if (phProv)
CryptReleaseContext(phProv, 0);
return v6;
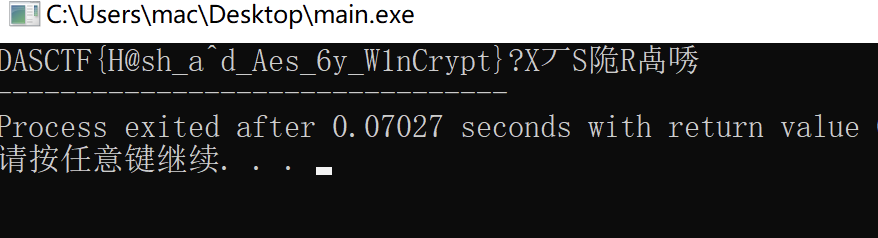
}
奇怪的交易
首先先查看文件信息,发现有upx壳,直接在kali用upx -d脱了
打开文件,发现一堆py开头的函数,推测是py打包的elf文件
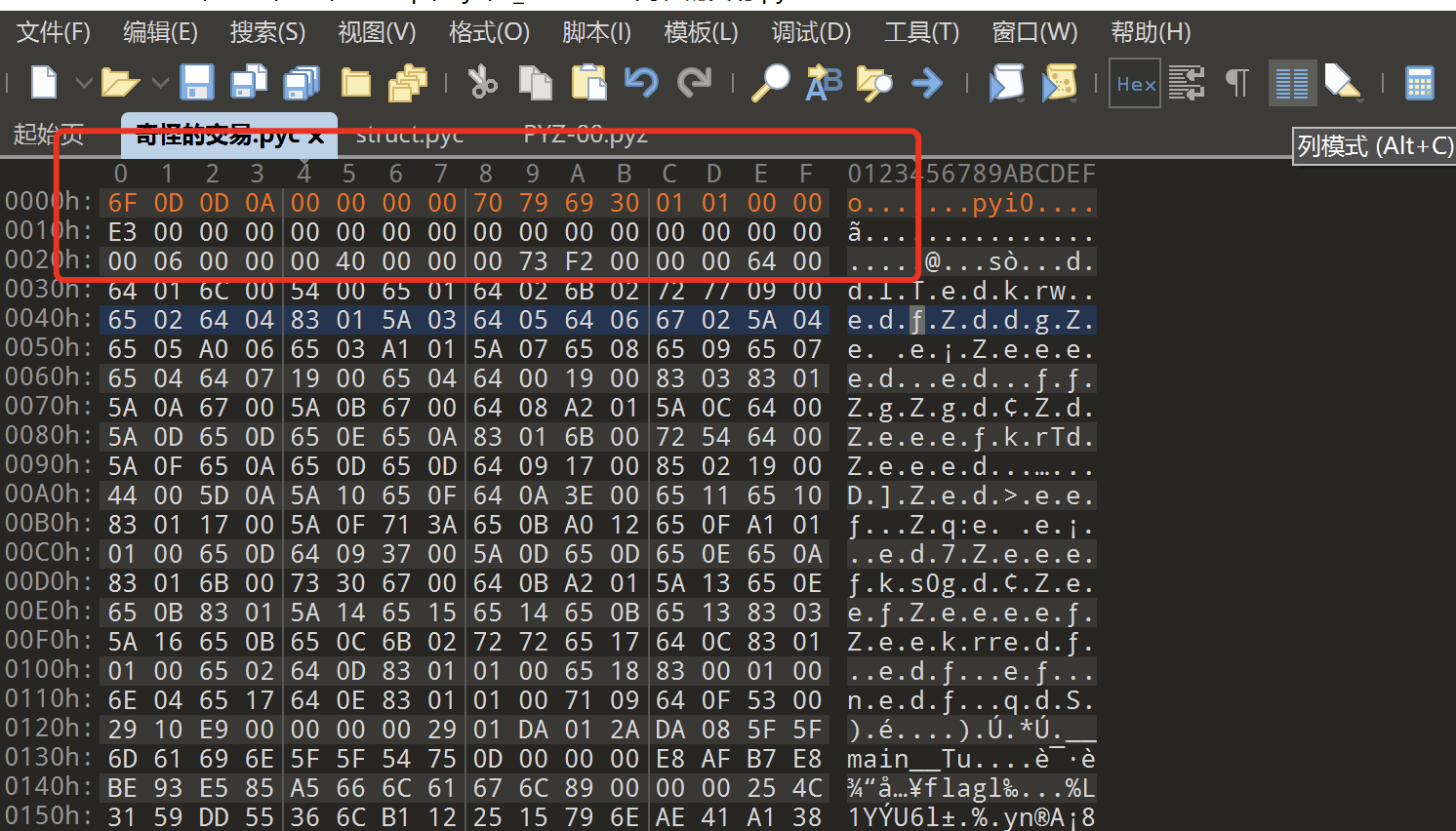
利用python pyinstxtractor.py 文件名 指令获取解包后的文件,此时的pyc文件并不能直接被网站或者脚本反编译,需要修复头部的若干内容,这16个字节从struct.pyc中获得,然后进行反编译
#!/usr/bin/env python
# visit https://tool.lu/pyc/ for more information
# Version: Python 3.10
from cup import *
if __name__ == '__main__':
flag = input('\xe8\xaf\xb7\xe8\xbe\x93\xe5\x85\xa5flag')
pub_key = [
0x649EE967E7916A825CC9FD3320BEABF263BEAC68C080F52824A0F521EDB6B78577EC52BF1C9E78F4BB71192F9A23F1A17AA76E5979E4D953329D3CA65FB4A71DA57412B59DFD6AEDF0191C5555D3E5F582B81B5E6B23163E9889204A81AFFDF119FE25C92F4ED59BD3285BCD7AAE14824240D2E33C5A97848F4EB7AAC203DE6330D2B4D8FF61691544FBECD120F99A157B3D2F58FA51B2887A9D06CA383C44D071314A12B17928B96F03A06E959A5AFEFA0183664F52CD32B9FC72A04B45913FCB2D5D2D3A415A14F611CF1EAC2D6C785142A8E9CC41B67A6CD85001B06EDB8CA767D367E56E0AE651491BF8A8C17A38A1835DB9E4A9292B1D86D5776C98CC25L,
0x647327833ACFEF1F9C83E74E171FC300FA347D4A6769476C33DA82C95120ACB38B62B33D429206FE6E9BB0BB7AB748A1036971BEA36EC47130B749C1C9FF6FE03D0F7D9FC5346EB0E575BDFA6C530AA57CD676894FC080D2DD049AB59625F4B9C78BCFD95CDCD2793E440E26E189D251121CB6EB177FEDB596409034E8B0C5BBD9BD9342235DBB226C9170EFE347FF0FD2CFF9A1F7B647CC83E4D8F005FD7125A89251C768AFE70BDD54B88116814D5030F499BCAC4673CCCC342FB4B6AC58EA5A64546DC25912B6C430529F6A7F449FD96536DE269D1A1B015A4AC6B6E46EE19DCE8143726A6503E290E4BAE6BD78319B5878981F6CFFDB3B818209341FD68BL]
m = libnum.s2n(flag)
c = str(pow(m, pub_key[1], pub_key[0]))
ᘡ = []
ᘙ = [
0xD28ED952L,
1472742623,
0xD91BA938L,
0xF9F3BD2DL,
0x8EF8E43DL,
617653972,
1474514999,
1471783658,
1012864704,
0xD7821910L,
993855884,
438456717,
0xC83555B7L,
0xE8DFF468L,
198959101,
0xC5B84FEBL,
0xD9F837C6L,
613157871,
0x8EFA4EDDL,
97286225,
0x8B4B608CL,
1471645170,
0xC0B62792L,
583597118,
0xAAB1C22DL,
0xBDB9C266L,
1384330715,
0xAE9F9816L,
0xD1F40B3CL,
0x8206DDC3L,
0xC4E0BADCL,
0xE407BD26L,
145643141,
0x8016C6A5L,
0xAF4AB9D3L,
506798154,
994590281,
0x85082A0BL,
0xCA0BC95AL,
0xA7BE567CL,
1105937096,
1789727804,
0xDFEFB591L,
0x93346B38L,
1162286478,
680814033,
0xAEE1A7A2L,
0x80E574AEL,
0xF154F55FL,
2121620700,
0xFCBDA653L,
0x8E902444L,
0xCA742E12L,
0xB8424071L,
0xB4B15EC2L,
0x943BFA09L,
0xBC97CD93L,
1285603712,
798920280,
0x8B58328FL,
0xF9822360L,
0xD1FD15EEL,
1077514121,
1436444106,
0xA2D6C17EL,
1507202797,
500756149,
198754565,
0x8E014807L,
880454148,
1970517398,
0xBFC6EE25L,
1161840191,
560498076,
1782600856,
0x9D93FEBEL,
1285196205,
788797746,
1195724574,
0xF2174A07L,
103427523,
0x952BFE83L,
0xF730AC4CL,
617564657,
978211984,
1781482121,
0x8379D23AL,
0xEAD737EEL,
0xE41555FBL,
659557668,
0x99F3B244L,
1561884856,
0x842C31A4L,
1189296962,
169145316,
0xA5CE044CL,
1323893433,
824667876,
408202876,
0xE0178482L,
0xF412BBBCL,
1508996065,
162419237,
0xDE740B00L,
0xB7CB64FDL,
0xEBCADB1FL,
0x8EAE2326L,
0x933C216CL,
0xD7D1F649L,
481927014,
0xA448AC16L,
0xBC082807L,
1261069441,
2063238535,
0x8474A61DL,
101459755,
0xBC5654D1L,
1721190841,
1078395785,
176506553,
0xD3C5280FL,
1566142515,
1938949000,
1499289517,
0xC59872F8L,
829714860,
0xE51502A2L,
952932374,
1283577465,
2045007203,
0xEBE6A798L,
0xE09575CDL,
0xADDF4157L,
0xC4770191L,
482297421,
1734231412,
0xDAC71054L,
0x99807E43L,
0xA88D74B1L,
0xCB77E028L,
1533519803,
0xEEEBC3B6L,
0xE7E680E5L,
272960248,
317508587,
0xC4B10CDCL,
0x91776399L,
27470488,
1666674386,
1737927609,
750987808,
0x8E364D8FL,
0xA0985A77L,
562925334,
0x837D6DC3L]
i = 0
if i < len(c):
ᘞ = 0
ᘡ.append(ᘞ)
i += 4
if not i < len(c):
ᘝ = [
54,
54,
54,
54]
ᘠ = len(ᘡ)
res = encrypt(ᘠ, ᘡ, ᘝ)
if ᘡ == ᘙ:
print('You are right!')
input('')
quit()
else:
print('Why not drink a cup of tea and have a rest?')
continue
逻辑存在问题,需要我们通过pycdump获取python的字节码,手撸字节码,补充逻辑
>>> import dis,marshal
>>> f=open('a.pyc', 'rb').read()
>>> co=marshal.loads(f[16:])
>>> dis.dis(co)可以读取字节码
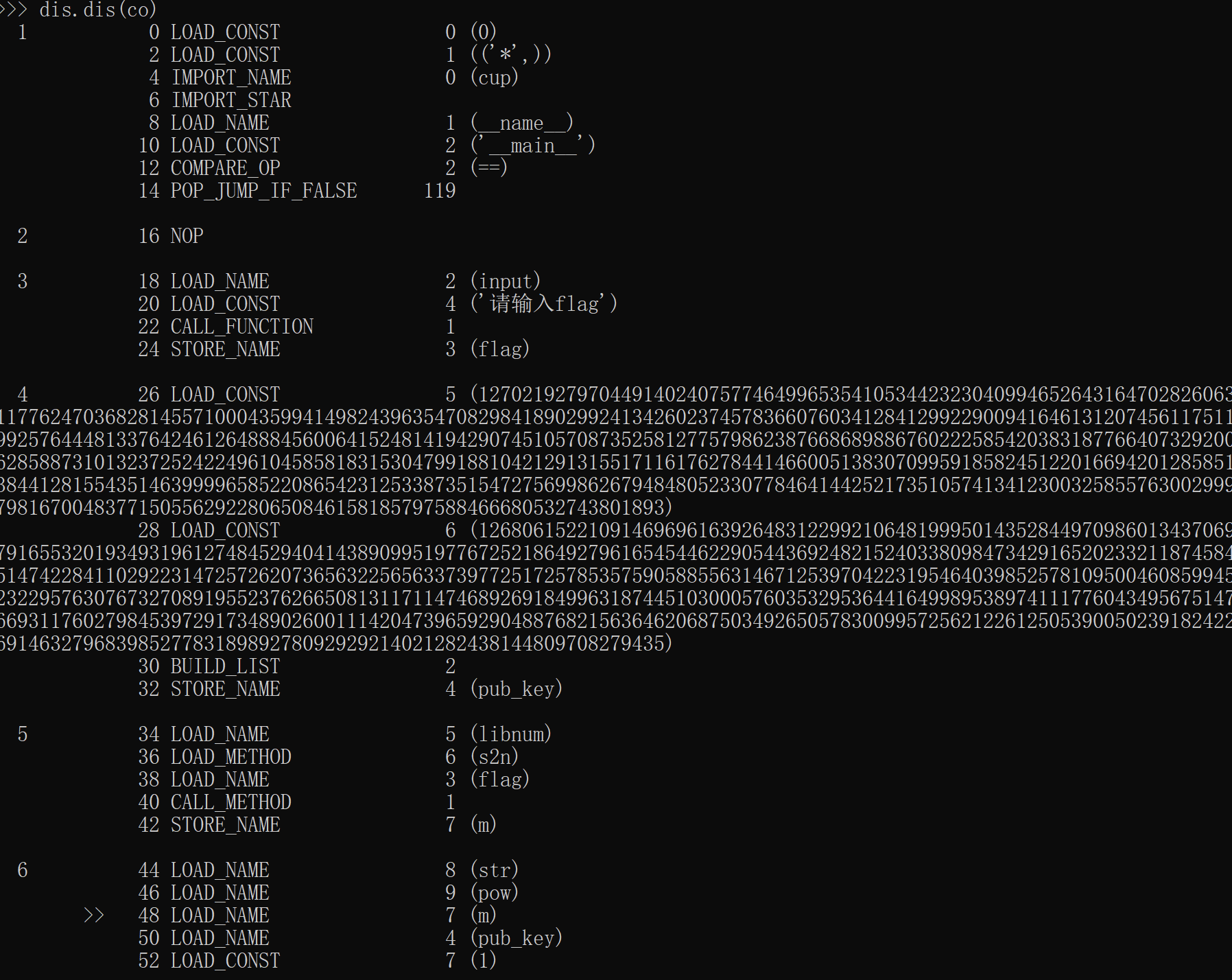
#!/usr/bin/env python
# visit https://tool.lu/pyc/ for more information
# Version: Python 3.10
from cup import *
if __name__ == '__main__':
flag = input('请输入flag')
pub_key = [
0x649EE967E7916A825CC9FD3320BEABF263BEAC68C080F52824A0F521EDB6B78577EC52BF1C9E78F4BB71192F9A23F1A17AA76E5979E4D953329D3CA65FB4A71DA57412B59DFD6AEDF0191C5555D3E5F582B81B5E6B23163E9889204A81AFFDF119FE25C92F4ED59BD3285BCD7AAE14824240D2E33C5A97848F4EB7AAC203DE6330D2B4D8FF61691544FBECD120F99A157B3D2F58FA51B2887A9D06CA383C44D071314A12B17928B96F03A06E959A5AFEFA0183664F52CD32B9FC72A04B45913FCB2D5D2D3A415A14F611CF1EAC2D6C785142A8E9CC41B67A6CD85001B06EDB8CA767D367E56E0AE651491BF8A8C17A38A1835DB9E4A9292B1D86D5776C98CC25L,
0x647327833ACFEF1F9C83E74E171FC300FA347D4A6769476C33DA82C95120ACB38B62B33D429206FE6E9BB0BB7AB748A1036971BEA36EC47130B749C1C9FF6FE03D0F7D9FC5346EB0E575BDFA6C530AA57CD676894FC080D2DD049AB59625F4B9C78BCFD95CDCD2793E440E26E189D251121CB6EB177FEDB596409034E8B0C5BBD9BD9342235DBB226C9170EFE347FF0FD2CFF9A1F7B647CC83E4D8F005FD7125A89251C768AFE70BDD54B88116814D5030F499BCAC4673CCCC342FB4B6AC58EA5A64546DC25912B6C430529F6A7F449FD96536DE269D1A1B015A4AC6B6E46EE19DCE8143726A6503E290E4BAE6BD78319B5878981F6CFFDB3B818209341FD68BL]
m = libnum.s2n(flag)
c = str(pow(m, pub_key[1], pub_key[0]))
flag1 = []
encodeflag = [
0xD28ED952L,
1472742623,
0xD91BA938L,
0xF9F3BD2DL,
0x8EF8E43DL,
617653972,
1474514999,
1471783658,
1012864704,
0xD7821910L,
993855884,
438456717,
0xC83555B7L,
0xE8DFF468L,
198959101,
0xC5B84FEBL,
0xD9F837C6L,
613157871,
0x8EFA4EDDL,
97286225,
0x8B4B608CL,
1471645170,
0xC0B62792L,
583597118,
0xAAB1C22DL,
0xBDB9C266L,
1384330715,
0xAE9F9816L,
0xD1F40B3CL,
0x8206DDC3L,
0xC4E0BADCL,
0xE407BD26L,
145643141,
0x8016C6A5L,
0xAF4AB9D3L,
506798154,
994590281,
0x85082A0BL,
0xCA0BC95AL,
0xA7BE567CL,
1105937096,
1789727804,
0xDFEFB591L,
0x93346B38L,
1162286478,
680814033,
0xAEE1A7A2L,
0x80E574AEL,
0xF154F55FL,
2121620700,
0xFCBDA653L,
0x8E902444L,
0xCA742E12L,
0xB8424071L,
0xB4B15EC2L,
0x943BFA09L,
0xBC97CD93L,
1285603712,
798920280,
0x8B58328FL,
0xF9822360L,
0xD1FD15EEL,
1077514121,
1436444106,
0xA2D6C17EL,
1507202797,
500756149,
198754565,
0x8E014807L,
880454148,
1970517398,
0xBFC6EE25L,
1161840191,
560498076,
1782600856,
0x9D93FEBEL,
1285196205,
788797746,
1195724574,
0xF2174A07L,
103427523,
0x952BFE83L,
0xF730AC4CL,
617564657,
978211984,
1781482121,
0x8379D23AL,
0xEAD737EEL,
0xE41555FBL,
659557668,
0x99F3B244L,
1561884856,
0x842C31A4L,
1189296962,
169145316,
0xA5CE044CL,
1323893433,
824667876,
408202876,
0xE0178482L,
0xF412BBBCL,
1508996065,
162419237,
0xDE740B00L,
0xB7CB64FDL,
0xEBCADB1FL,
0x8EAE2326L,
0x933C216CL,
0xD7D1F649L,
481927014,
0xA448AC16L,
0xBC082807L,
1261069441,
2063238535,
0x8474A61DL,
101459755,
0xBC5654D1L,
1721190841,
1078395785,
176506553,
0xD3C5280FL,
1566142515,
1938949000,
1499289517,
0xC59872F8L,
829714860,
0xE51502A2L,
952932374,
1283577465,
2045007203,
0xEBE6A798L,
0xE09575CDL,
0xADDF4157L,
0xC4770191L,
482297421,
1734231412,
0xDAC71054L,
0x99807E43L,
0xA88D74B1L,
0xCB77E028L,
1533519803,
0xEEEBC3B6L,
0xE7E680E5L,
272960248,
317508587,
0xC4B10CDCL,
0x91776399L,
27470488,
1666674386,
1737927609,
750987808,
0x8E364D8FL,
0xA0985A77L,
562925334,
0x837D6DC3L]
i = 0
if i < len(c):
x = 0
for ii in c[i:i+4]:
x = x<<8+ord(ii)
flag1.append(x)
i=i+4
if not i < len(c):
key = [54,54,54, 54]
len = len(flag1)
res = encrypt(len, flag1, key)
if flag1 == encodeflag:
print('You are right!')
input('')
quit()
else:
print('Why not drink a cup of tea and have a rest?')
continue
已经修复完了,但是我们不知道encrypt的加密方式,因为这个是来自cup这个包,这个包是作者自己导入的
关于pyinstaller打包这篇博客写的很详细
有-key参数的逆向,将py编译成pyc,然后部分压缩成pyz,程序再通过对pyc和pyz的调用,那么问题来了,cup这个包在pyz文件夹中,但是我们pyinstxtractor后,文件是空的,因为我们需要有相同的python环境,本程序的python环境是3.10
我又下了个python3.10
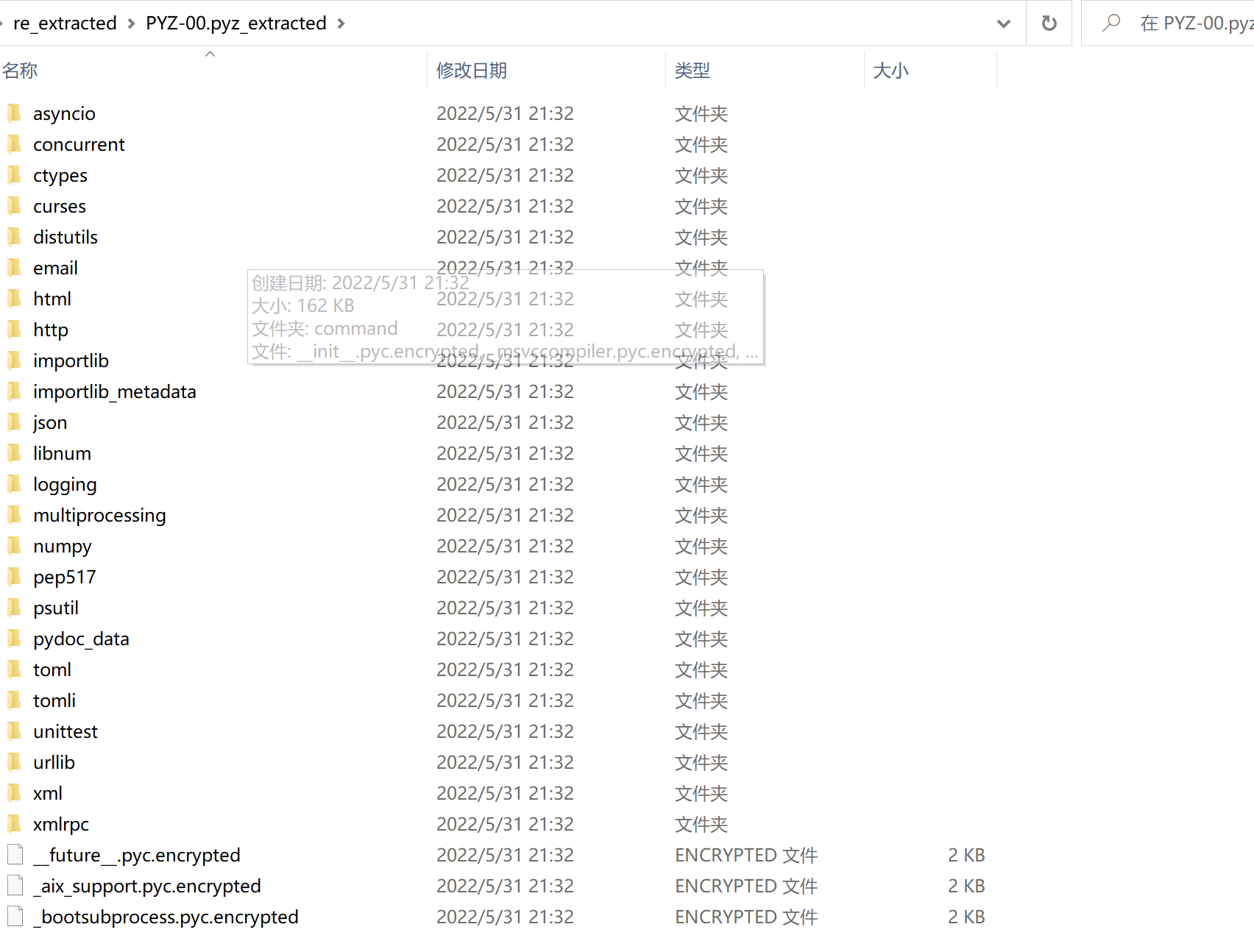
我们反编译archive.pyc可以看出pyinstxtractor使用tinyAes加密我们的cup包,有现成的解密脚本可以套
import tinyaes
import zlib
CRYPT_BLOCK_SIZE = 16
# 从crypt_key.pyc获取key,也可自行反编译获取
key = bytes('0000000000000tea', 'utf-8')
inf = open('cup.pyc.encrypted', 'rb') # 打开加密文件
outf = open('output.pyc', 'wb') # 输出文件
# 按加密块大小进行读取
iv = inf.read(CRYPT_BLOCK_SIZE)
cipher = tinyaes.AES(key, iv)
# 解密
plaintext = zlib.decompress(cipher.CTR_xcrypt_buffer(inf.read()))
# 补pyc头(最后自己补也行)
outf.write(b'\x6f\x0d\x0d\x0a\0\0\0\0\0\0\0\0\0\0\0\0')
# 写入解密数据
outf.write(plaintext)
inf.close()
outf.close()密钥需要我们反汇编crypto_key.pyc文件
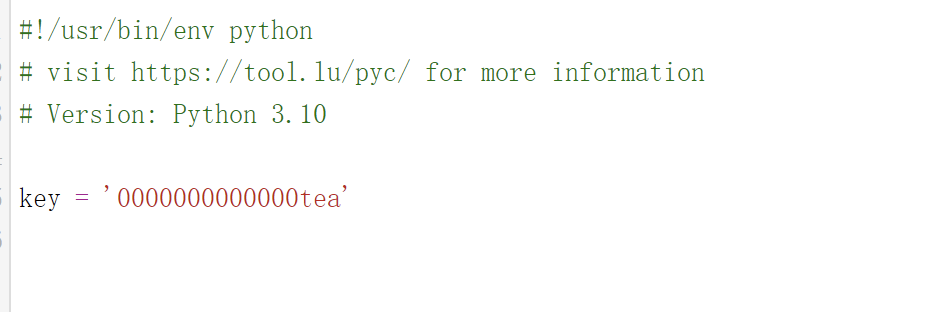
现在就需要解包
反编译后是一个没有任何修改的xxtea
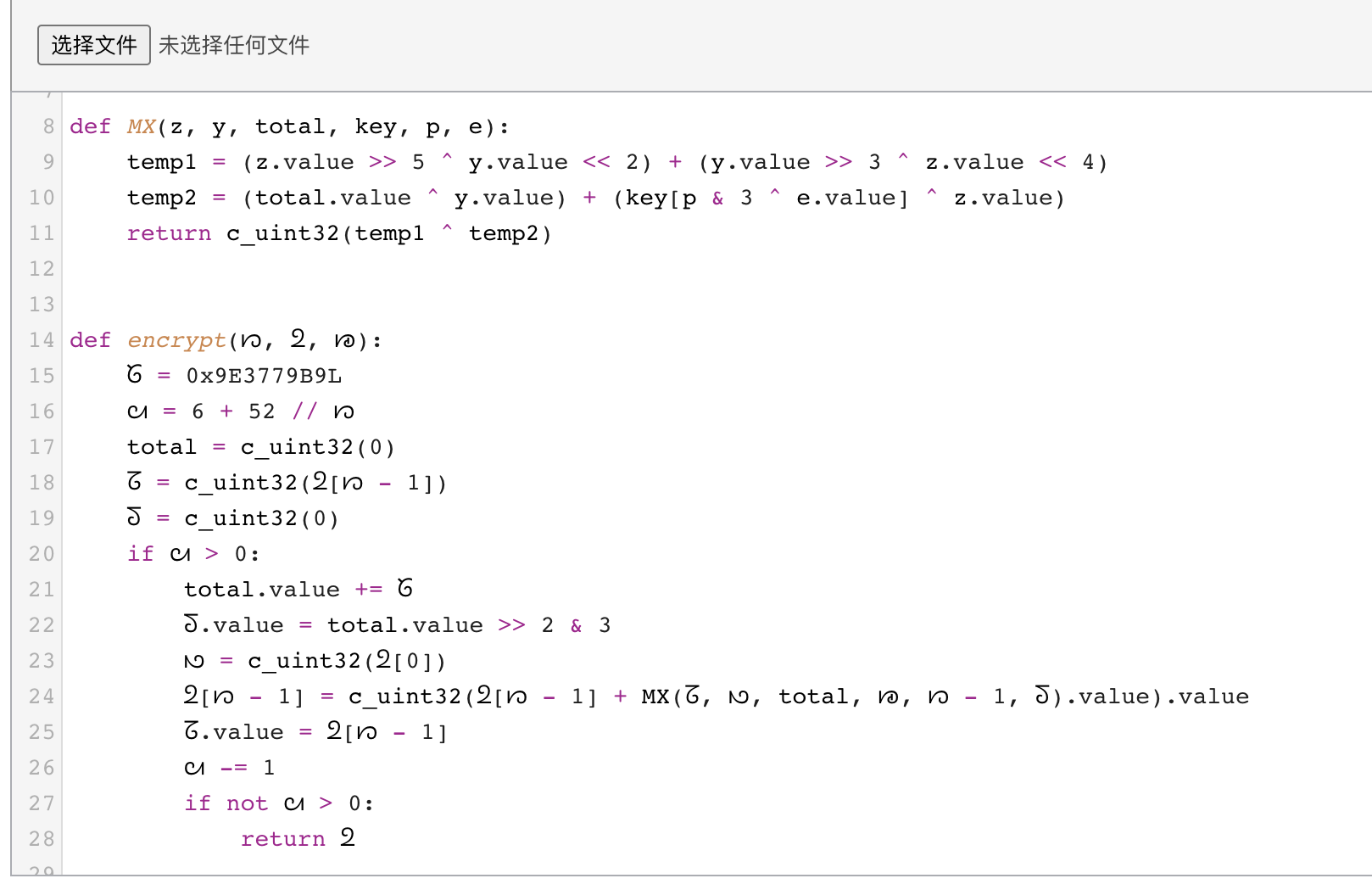
所以我们先解xxtea,得到rsa加密的密文,再解rsa
#include <stdio.h>
#include <stdlib.h>
#define DELTA 0x9e3779b9//0x61C88647
int main()
{
unsigned int v[] = {3532577106, 1472742623, 3642468664, 4193500461, 2398676029, 617653972, 1474514999, 1471783658, 1012864704, 3615627536, 993855884, 438456717,
3358938551, 3906991208, 198959101, 3317190635, 3656923078, 613157871, 2398768861, 97286225, 2336972940, 1471645170, 3233163154, 583597118, 2863776301,
3183067750, 1384330715, 2929694742, 3522431804, 2181488067, 3303062236, 3825712422, 145643141, 2148976293, 2940910035, 506798154, 994590281, 2231904779,
3389770074, 2814269052, 1105937096, 1789727804, 3757028753, 2469686072, 1162286478, 680814033, 2934024098, 2162521262, 4048876895, 2121620700, 4240287315,
2391811140, 3396611602, 3091349617, 3031523010, 2486958601, 3164065171, 1285603712, 798920280, 2337813135, 4186055520, 3523024366, 1077514121, 1436444106,
2731983230, 1507202797, 500756149, 198754565, 2382448647, 880454148, 1970517398, 3217485349, 1161840191, 560498076, 1782600856, 2643721918, 1285196205,
788797746, 1195724574, 4061612551, 103427523, 2502688387, 4147162188, 617564657, 978211984, 1781482121, 2205798970, 3939973102, 3826603515, 659557668,
2582884932, 1561884856, 2217488804, 1189296962, 169145316, 2781742156, 1323893433, 824667876, 408202876, 3759637634, 4094868412, 1508996065, 162419237,
3732146944, 3083560189, 3955940127, 2393776934, 2470191468, 3620861513, 481927014, 2756226070, 3154651143, 1261069441, 2063238535, 2222237213, 101459755,
3159774417, 1721190841, 1078395785, 176506553, 3552913423, 1566142515, 1938949000, 1499289517, 3315102456, 829714860, 3843359394, 952932374, 1283577465,
2045007203, 3957761944, 3767891405, 2917089623, 3296133521, 482297421, 1734231412, 3670478932, 2575334979, 2827842737, 3413631016, 1533519803,
4008428470, 3890643173, 272960248, 317508587, 3299937500, 2440520601, 27470488, 1666674386, 1737927609, 750987808, 2385923471, 2694339191, 562925334,
2206035395};
unsigned int key[] = {54,54,54,54};
unsigned int sum = 0;
unsigned int y,z,p,rounds,e;
int n = 155; //
int i = 0;
rounds = 6 + 52/n;
y = v[0];
sum = (rounds*DELTA)&0xffffffff;
do
{
e = sum >> 2 & 3;
for(p=n-1;p>0;p--)
{
z = v[p-1];
v[p] = (v[p] - ((((z>>5)^(y<<2))+((y>>3)^(z<<4))) ^ ((key[(p^e)&3]^z)+(y ^ sum)))) & 0xffffffff;
y = v[p];
}
z = v[n-1];
v[0] = (v[0] - (((key[(p^e)&3]^z)+(y ^ sum)) ^ (((y<<2)^(z>>5))+((z<<4)^(y>>3))))) & 0xffffffff;
y = v[0];
sum = (sum-DELTA)&0xffffffff;
}while(--rounds);
for(i=0;i<n;i++)
{
printf("%u",v[i]);
}
return 0;
}
#825243185 808661814 892548151 892941616 892876857 909129523 960049970 842217527 825702707 825636663 825505848 876163635 876032567 876033073 959526968 909260343 943077682 892352569 892547384 892876598 892809273 942748210 926234676 808465462 926299448 808858163 892678966 909391921 943207731 909653561 858992688 875706672 808925233 892548658 808531512 808793142 909455416 909391416 875640629 875639608 842543668 925906993 808727608 808990770 892811058 808465714 959984178 959854645 858863412 858796082 858796345 859058993 808662073 808465715 875639088 875968822 943208249 875770168 842020660 876032818 959985205 809054259 892612916 959723825 942814774 942814000 859257144 875574580 926365753 808662582 909389878 892613945 942683445 925906740 842086705 909260083 909129015 825505328 959461173 942748984 825374769 943273008 909129523 942684466 842412854 825504821 808728114 842347826 876163383 808991028 859060281 926496055 858796339 959853875 875901237 959853621 876033078 842281525 925972786 808794161 959657010 825700918 909719609 959788086 959853874 842084408 875575608 909717560 959657527 842348853 959853105 842610743 959460401 892352313 808661553 808990001 925906487 959657784 942879025 875901497 926103350 959657272 875902263 909195568 926101555 909325113 892744498 842610482 892416053 808464949 858796089 808989497 842151736 825832244 875574839 858863155 859256117 875640887 892549173 943272752 876033589 926299954 808990516 842086707 892941366 909455411 892549177 858862391 825504820 876032051 808661305 859123763 926102329 842018867 57中间还有一层是左移的操作,没想到怎么逆写算法,直接爆破吧
a=[825243185,808661814,892548151,892941616,892876857,909129523,960049970,842217527,825702707,825636663,825505848,876163635,876032567,876033073,959526968,909260343,943077682,892352569,892547384,892876598,892809273,942748210,926234676,808465462,926299448,808858163,892678966,909391921,943207731,909653561,858992688,875706672,808925233,892548658,808531512,808793142,909455416,909391416,875640629,875639608,842543668,925906993,808727608,808990770,892811058,808465714,959984178,959854645,858863412,858796082,858796345,859058993,808662073,808465715,875639088,875968822,943208249,875770168,842020660,876032818,959985205,809054259,892612916,959723825,942814774,942814000,859257144,875574580,926365753,808662582,909389878,892613945,942683445,925906740,842086705,909260083,909129015,825505328,959461173,942748984,825374769,943273008,909129523,942684466,842412854,825504821,808728114,842347826,876163383,808991028,859060281,926496055,858796339,959853875,875901237,959853621,876033078,842281525,925972786,808794161,959657010,825700918,909719609,959788086,959853874,842084408,875575608,909717560,959657527,842348853,959853105,842610743,959460401,892352313,808661553,808990001,925906487,959657784,942879025,875901497,926103350,959657272,875902263,909195568,926101555,909325113,892744498,842610482,892416053,808464949,858796089,808989497,842151736,825832244,875574839,858863155,859256117,875640887,892549173,943272752,876033589,926299954,808990516,842086707,892941366,909455411,892549177,858862391,825504820,876032051,808661305,859123763,
926102329,842018867]
cc=""
x=0
arr = "0123456789"
def test():
global cc
global x
if x==154:#最后一位特殊考虑
for q in arr:
guess = q
s = 0
for ii in guess:
s = (s << 8) + ord(ii)
if s == 57:
cc += guess
return
for q in arr:
for b in arr:
for c in arr:
for d in arr:
guess=q+b+c+d
s=0
for ii in guess:
s=(s<<8)+ord(ii)
if s==a[x]:
cc+=guess
x+=1
return
while x<len(a):
test()
print(cc)
#10610336534759505889607399322387179316771488492347274741918862678692508953185876570981227584004676580623553664818853686933004290078153620168054665086468417541382824708104480882577200529822968531743002301934310349005341104696887943182074473298650903541494918266823037984054778903666406545980557074219162536057146090758158128189406073809226361445046225524917089434897957301396534515964547462425719205819342172669899546965221084098690893672595962129879041507903210851706793788311452973769358455761907303633956322972510500253009083922781934406731633755418753858930476576720874219359466503538931371444470303193503733920039现在只剩最后一步解RSA!但是我不会,贴个t0hka1师傅的脚本
import gmpy2
from Crypto.PublicKey import RSA
import ContinuedFractions, Arithmetic
from Crypto.Util.number import long_to_bytes
def wiener_hack(e, n):
# firstly git clone https://github.com/pablocelayes/rsa-wiener-attack.git !
frac = ContinuedFractions.rational_to_contfrac(e, n)
convergents = ContinuedFractions.convergents_from_contfrac(frac)
for (k, d) in convergents:
if k != 0 and (e * d - 1) % k == 0:
phi = (e * d - 1) // k
s = n - phi + 1
discr = s * s - 4 * n
if (discr >= 0):
t = Arithmetic.is_perfect_square(discr)
if t != -1 and (s + t) % 2 == 0:
return d
return False
def main():
pub_key = [
0x649EE967E7916A825CC9FD3320BEABF263BEAC68C080F52824A0F521EDB6B78577EC52BF1C9E78F4BB71192F9A23F1A17AA76E5979E4D953329D3CA65FB4A71DA57412B59DFD6AEDF0191C5555D3E5F582B81B5E6B23163E9889204A81AFFDF119FE25C92F4ED59BD3285BCD7AAE14824240D2E33C5A97848F4EB7AAC203DE6330D2B4D8FF61691544FBECD120F99A157B3D2F58FA51B2887A9D06CA383C44D071314A12B17928B96F03A06E959A5AFEFA0183664F52CD32B9FC72A04B45913FCB2D5D2D3A415A14F611CF1EAC2D6C785142A8E9CC41B67A6CD85001B06EDB8CA767D367E56E0AE651491BF8A8C17A38A1835DB9E4A9292B1D86D5776C98CC25,
0x647327833ACFEF1F9C83E74E171FC300FA347D4A6769476C33DA82C95120ACB38B62B33D429206FE6E9BB0BB7AB748A1036971BEA36EC47130B749C1C9FF6FE03D0F7D9FC5346EB0E575BDFA6C530AA57CD676894FC080D2DD049AB59625F4B9C78BCFD95CDCD2793E440E26E189D251121CB6EB177FEDB596409034E8B0C5BBD9BD9342235DBB226C9170EFE347FF0FD2CFF9A1F7B647CC83E4D8F005FD7125A89251C768AFE70BDD54B88116814D5030F499BCAC4673CCCC342FB4B6AC58EA5A64546DC25912B6C430529F6A7F449FD96536DE269D1A1B015A4AC6B6E46EE19DCE8143726A6503E290E4BAE6BD78319B5878981F6CFFDB3B818209341FD68B]
# 0->n,1->e
n = pub_key[0]
e = pub_key[1]
c = 10610336534759505889607399322387179316771488492347274741918862678692508953185876570981227584004676580623553664818853686933004290078153620168054665086468417541382824708104480882577200529822968531743002301934310349005341104696887943182074473298650903541494918266823037984054778903666406545980557074219162536057146090758158128189406073809226361445046225524917089434897957301396534515964547462425719205819342172669899546965221084098690893672595962129879041507903210851706793788311452973769358455761907303633956322972510500253009083922781934406731633755418753858930476576720874219359466503538931371444470303193503733920039
d = wiener_hack(e, n)
m = pow(c, d, n)
print(long_to_bytes(m)) # flag{You_Need_Some_Tea}
if __name__ == "__main__":
main()转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至 767778848@qq.com